The Middle East Joins the SCADA / ICS Standards Foray
The oil rich countries in the Middle East depend on Industrial Control Systems (ICS) to run the Energy sector which is responsible in average for generating around 70-90 % of the national GDP. and ultimately providing around 40% of the world’s total energy consumption.
Since STUXNET news surfaced 18 month ago, the region has witnessed not less than 20 different information and cyber security conferences that addressed the topic and highlighted the ICS security issue as a monumental risk to the GCC region in particular.
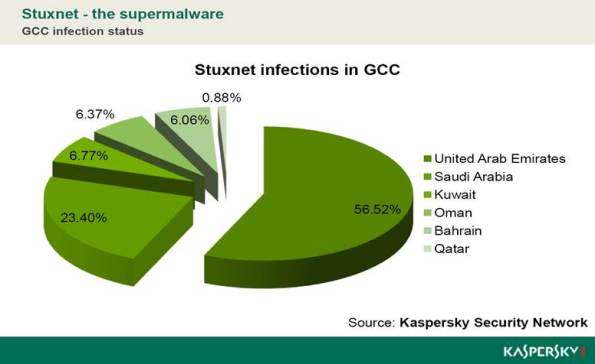
The Kaspersky chart below show STUXNET infection rates in the GCC countries,(UAE,Saudi,Kuwait,Bahrain,Qatar and Oman).
and recently the state of Qatar through the national CERT issued the region’s first national level ICS security Guidelines in Arabic as well as an English translated version. currently the document “planned to be updated annually” is not mandatory but the document’s roadmap is likely to see a change in the next few years.
You can download a copy of the English translation here (Download)
Press Coverage – Here
SCADA Security Evaporates in Texas
A hacker, going with the name “pr0f” has been all over the news for showing that he was able to access a SCADA system used in Texas. only to vent his anger on how the DHS underplayed a recent attack that destroyed a pump at a water facility in Illinois.
Comment: Looking into the images, in addition to South Huston Texas,they also feature screen shots labelled as (City of South Huston Nevada and Virginia)
In one of his interviews, “pr0f” said that he was able to access the systems via “two” different methods. First through a VNC connection that was accessible from the internet !!!, which helped him take the screen shots below, in addition to the ability to access the web administration portal which is still accessible till this morning !!.
Screen shots:
When asked to comment on the Illinois incident, he said
“I dislike, immensely, how the DHS tend to downplay how absolutely (expletive) the state of national infrastructure is. I’ve also seen various people doubt the possibility an attack like this could be done,”
apparently Using a Romanian email (pr0f_srs@ue.co.ro) to post the screenshots on pastebin , the hacker told Threatpost that he discovered the vulnerable system using a scanner that looks for the online fingerprints of SCADA systems. He said South Houston had an instance of the Siemens Simatic human machine interface (HMI) software that was accessible from the Internet and that was protected with an easy-to-hack, three character password.!!!” No Comment”.
Actually there are a couple of comments:
– He might have used a publicly discussed vulnerability in Siemens allowing attackers to intercept and figure-out passwords, or change the configuration of the PLCs. So my guess is that using a harder password would not have helped much.
— the Siemens Advisory that went out last July (http://support.automation.siemens.com/WW/llisapi.dll?func=cslib.csinfo&lang=en&objid=51401544&caller=view) tells you to limit physical and logical access to the vulnerable system while they work on a patch ( which is yet still to come).
– WHY….is the system accessible from the internet? is the real question.
— I just can’t get why would someone put his critical business asset even if its an ice cream machine online and accessible from the internet…apparently not hardened ” system fingerprint was searchable” and with lots of Siemens vulnerabilities/goodies up for grabs.
“pr0f” is probably going to face some serious legal troubles for admitting his act, but his adventure makes me wonder…if this is the status of security and awareness in “some” of the critical infrastructures in the united states of america and I’m sure in other “developed” countries.
What would be the status of SCADA security in the “Developing” world ? I am making a study on the CIIP status in the developing world and found that in just one domain/sector which is oil production as of November 2010, the OPEC members “ 12 countries all considered developing countries” collectively hold 79% of the world’s crude oil reserves and 44% of the world’s crude oil production with 100% reliance on SCADA/DCS systems many of which has reported vulnerabilities or even exploits, none of those countries has a national CIIP strategy or follow/adopt an acknowledged SCADA security guideline or best practice or even consider Critical Information Infrastructure Protection a topic worthy of discussion.
DHS: “Anonymous” Sniffing around SCADA systems
A recently leaked DHS document (Download Here) warns that Hacktivist group “Anonymous” are considering attacking SCADA systems and Critical Infrastructures in some countries.
The document labelled as “for official use only” quotes several “twitter” posts believed to belong to Anonymous members discussing and exchanging information about SCADA projects.
” On 19 July 2011, a known Anonymous member posted to Twitter the results of browsing the directory tree for Siemens SIMATIC software. This is an indication in a shift toward interest in control systems by the hacktivist group.”
another tweet
“An anonymous individual provided an open source posting on twitter of xml and html code that queries the SIMATIC software. The individual alleged access to multiple control systems and referred to “Owning” them.2 The Twitter posting does not identify any systems where privileged levels of access to control systems have been obtained.”
My Comments:
The report insinuates that experienced Anonymous hackers can quickly gain the knowledge required to hack ICS “Industrial Control Systems” which is correct. But the report didn’t mention the fact that currently there is a gold rush amongst researchers to come up with SCADA vulnerabilities, just in the past couple of weeks anyone following the right and publicly available sources can count more than a dozen zero-day vulnerabilities out there (I mean with no patch available).couple that with high motivation and you have a dangerous formula.
Just by looking around, I am afraid to say that ICS are going to be the next target after the current wave of attacks on financial institutions “Occupy wall-street”.
Looking at the flow of events, Anonymous, LulzSec and Co. have already targeted Governments, Big corporates, Defense contractors,Banks and Stock exchanges….the next logical step down the food chain is Energy.
More on the topic:
Siemens SDLess – What CERTs talked about
Recently I attended the FIRST (Forum of Incident Response Security Teams) conference in Vienna which is the annual gathering for CERTs (Computer Emergency Response Teams) from around the world and everyone noticed that for the first time in the history of the 23 year old annual conference that the main buzzword was not some new IT security breakthrough, the most talked about vendor in the lobby and in the hallways was not Microsoft with all it’s glory, the hottest sessions were not F-SECURE’s Mikko H. Hypponen or Kaspersky’s Founder Eugene Kaspersky and the most talked about threat was not buffer overflow.
The answer for all of the above was one word…”SIEMENS”.
It was clear that things have changed and that there is a shift in the priorities of the attendees.and this is very alarming to see that in the FIRST conference specially.
The significance of the FIRST conference is that its in my opinion…the ultimate good guys gathering.
CERT teams are the real firefighters on the ground and usually those guys deal with all the dirt on a 24x7x365 basis and many of them do it country/regional level…also by design CERT staff are some of the most connected people in the information security business and most importantly they thrive on hard earned IT community trust. so if you hear them saying this is a game changer and most of us are not ready…this is your cyber strategy needs to be revised heads-up right here.
Also for the first time SIEMENS represented by SIEMENS-CERT was going to talk about Stuxnet from their perspective. although it was one of 3 parallel sessions i guess everyone in the conference was in this room to hear what SIEMENS have to say in its own defense regarding Stuxnet.
Prelude
They kickstarted the session by asking everyone not to copy anything from the slides and to stop using social media completely, the slides were all marked as CONFIDENTIAL…turned out that there is nothing they can add to what everybody knew.
Apology
SIEMENS said that they completely understand why they are being scrutinized and that they did a mistake handling the Stuxnet issue…yes they said “We did a mistake” and I have to credit them for that. the mistake in their presentation was Siemens CERT not sharing any of the information at hand “early on” with other CERTs or at least proactively explaining the issue to the Media properly, this is true but its not the root cause of the problem.
Stuxnet over the week end
SIEMENS CERT first heard about Stuxnet over the weekend and at first glance they thought it can wait till monday, they started to slowly unwrap the malware only to be beaten to it by Ralf Langner initial findings posted on his blog which started a media frenzy…in their own words it was a top decision not to enter the fray until they finish the entire analysis (took them 6 month)…but who can wait with such a gem at hand. and the rest is history.
SIEMENS View on how to improve security in the future
They said that as a vendor SIEMENS value security and couldn’t be less annoyed standing here having to clear/justify this mess, and that they promise to be more open and to issue alerts, customer specific notifications and patches much sooner if anything of such nature surfaced again.
What they didn’t say and should be saying
SIEMENS never came close to acknowledge that their entire design process which has always been flawed but survived due security by obscurity came to a sad end..and to make things worse…everybody (researchers, opportunists and criminals) is now trying to play with it maybe he/she stumbles upon something that can cause more embarrassment. they need to come clean and know that the only proper way to fix this kind of fundamentally poor design issues (Hard coded passwords, leaving unnecessary ports and services open…etc)…is a totally new SDL “Security Development Lifecycle” that would eventually allow them to spot things much early on and to avoid silly mistakes as in hard coding passwords in the year 2011.
Stuxnet Code: can be downloaded from Here (Important: After downloading – Change the extension name to .RAR)
Watch Ralf Langner talk in NATOs conference on cyber conflict
ICS-CERT alert on the hard coded credentials in SIEMENS products
Latvian Electricity Grid Hacked !! So claims a Chinese Group
A recent post in the full disclosure list (FDL) claims that a Latvian Power Plant called (Latvenergo RIGAS HES-2) has been hacked. the post is strikingly similar in its approach to the recent FPL SCADA incident/Hoax.
Similarities:
-The FPL post was sent to the FDL at 8:22 (-7) PDT
-The RIGAS post was sent to the FDL at 8:48 (-7) PDT
-The FPL email that the hacker BGR sent me was sent from a Yahoo account, this time they used Rocketmail.com (owned by Yahoo)
-Both started by posting real IPs owned by reportedly the victims
-Both posted Images/screen shots hosted at Imageshack.us
-Both pasted the Cisco router configuration files along with the passwords
The screen shots were taken from a windows PC that also shows a lotus notes mailbox named (Leva Vaica).
I would assume from the pop up below that this is an Asus Laptop and not a desktop, since the EPU-4 Engine is a mother board with integrated graphics mostly used in Asus Laptops for power saving.
Also you can see that xpower was used to view the SLDs (Single Line Diagrams) and they were stored under the same laptop local C:\ drive
The entire project was saved under the name of (Leva_Test).
A group called (China Youth Hackers Alliance) claimed responsibility.
Related news: This April 28th and in the same city of the power plant (Riga,Latvia) was the Chinese Business day and trade expo (Invest EXPO 2011)
This reported incident looks like an FPL Hoax “Deja vu” or the Chinese business convoy revenge for a business deal that turned sour 🙂
Florida Power and Light (FPL): – Sharing SCADA Secrets
***Update***
There has been some news that in this incident the alleged insider has faked some aspects / manipulated some screen shots to embarrass his former employers ” FPL”
Sources: Here
***End of Update***
On April 16th (15:43 GMT) I received the following email from (bgr_24423 AT Yahoo.com) :
Here comes my revenge for illegitimate firing from Florida Power & Light Company (FPL)
… ain’t nothing they can do with it, since NM electricity is turned off !!! In some days people will know about FLP SCADA security, you are one of the first …
The email was long and contained all the details that proves that this guy had hacked the system, he even posted the complete Configuration file from the central Cisco Router and Security Device Manager. along with the passwords.
To spice things up he included 8 URLs with screen shots to proof his point. (Image URLs below).
1) http://img838.imageshack.us/i/49986845.png/
2) http://img718.imageshack.us/i/24380855.png/
3) http://img24.imageshack.us/i/58868342.png/
4) http://img228.imageshack.us/i/85258364.png/
5) http://img163.imageshack.us/i/90736853.png/
6) http://img217.imageshack.us/i/55439027.png/
7) http://img40.imageshack.us/i/87526089.png/
8 ) http://img864.imageshack.us/i/94061747.png/
I immediately checked those image URLS but I found that they had (Zero Views) at the time….now its different.
Seeing that I am the first one to see the images, I had my doubts that it might be a fake email so i did some googling to make sure that its a real incident. to my surprise all my checks worked out.
Even the email header looked fine and it showed that the email was sent from outside the US…from Germany to be precise, which is only logical for an email of such nature. “go as far as possible from the crime scene is usually the international best practice”…or at least show that you are as far as possible.
The email header here :
At this point I decided to report everything to ICS-CERT. But now that the news is already everywhere I can publicly comment on the incident.
My Comments:
– I would assume that, he sent this email to some of the known and trusted SCADA security blogs out there, but the good thing is that none shared it publicly. “or at least thats my understanding”.
– He took the next step and shared it on the full disclosure mailing list – and then it was out of control.
– People tend to overlook the sensitivity of corporate or confidential information, once things turn personal.
– In few minutes Blogs and mailing lists around the globe had information about another country’s national Critical Infrastructure. It’s striking that what was once considered a secret that people or nations pay and recruit spies to get, is now free.
– Any lazy, couch potato spy can just sign up for a dozen of those mailing lists and he would do just fine.
– For how long would this information remain useful is FPL problem now.
– People will start discussing the configuration details this guy posted, and how insecure was their VLAN configurations…etc, but the question is how easy is it for an employee to have access to all this information.
– The router configuration file headers have the login banner of **Bellsouth** , Why ?
– Insider threat is the REAL deal, not anything else.
It’s worth mentioning that FPL made the headlines for the wrong reasons several times over the past 3 years, and they were fined by NERC more than once before, here is a quick account of the fines:
– March 31st 2009, A fine for 250,000 USD (NERC Notice of Penalty – HERE)
– March 5th 2010, A fine for 350,000 USD (FERC Penalty Notice)
– October 8th 2009, A fine for 25 Million USD (2008 Blackout settlement)
– April 2006, A fine for 130,000 USD for Sleeping guards (News)
Further more back in December 2009, Burns and McDonnel consultancy firm completed a cyber security assessment project where they handed recommendations to make FPL in compliance with NERC…This must be one useful report.
Burns & McDonnell has provided security assessments for Florida Power and Light (FPL), evaluating sites that have been considered critical assets under North American Electrical Reliability Corp. (NERC) standards for Critical Infrastructure Protection (CIP). Burns & McDonnell has made recommendations to ensure FPL is prepared to meet or exceed the NERC CIP guidelines in both physical and cyber security. These audits have included site visits and capturing system configurations to determine the current state of the security protections in place.
Source : Burns and McDonnell
Stuxnet: Introduction, Installation and Infection Video
Source: http://www.SCADAhacker.com/stuxnet
This demonstration video takes a detailed look at the Stuxnet worm on a Siemens PCS7 FieldPG host. The demo provides a brief overview of the worm, and then takes a look at how it exploits Windows vulnerabilities to install itself on the target host, infect various Windows and Siemens components, and then replicate itself for installation on other hosts.
Additional information available at This demonstration video takes a detailed look at the Stuxnet worm on a Siemens PCS7 FieldPG host. The demo provides a brief overview of the worm, and then takes a look at how it exploits Windows vulnerabilities to install itself on the target host, infect various Windows and Siemens components, and then replicate itself for installation on other hosts.
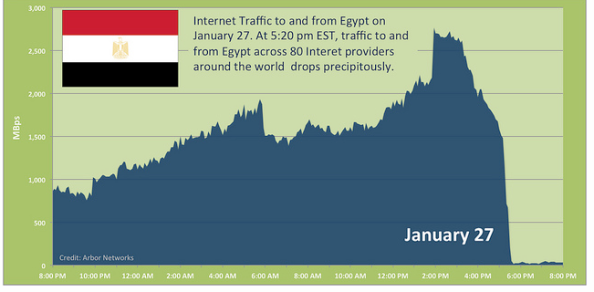
Egypt flipped the Internet Kill Switch – Total Blackout reported
In an attempt to stifle anti-government protests scheduled to take place nation wide tomorrow (January the 28th), reports and sources are confirming that the Egyptian government used the “Internet kill switch” for the first time in the world. as they ordered the ISPs and Mobile Carriers (Including multinationals like Vodafone) to pull the plug on…hmmm..the INTERNET.
So right now, more than Eighty Million Egyptians are going through probably the first internet blackout in the 21st century. even RIM’s blackberry users reported that they cant access the BIS browser and the BBM service.
A couple years ago and during similar anti-governemtn protests in 2009 and in 2010, the government of Iran blocked and restricted access to social media websites like twitter and facebook.
But this time the Egyptian government decided to take it a bit further because blocking particular websites and services was proven inadequate and/or useless as the 20 Million Egyptians with permanent ADSL internet access quickly overcame this blockage with proxies and TOR networks.
This is simply an unprecedented stupid decision.
Wikileaks Released a list of Critical Infrastructures world wide – as seen by the DHS
Wikileaks helped me answer a very important question on how countries see the critical infrastructure interdependencies across the globe, Would an attack on a Saudi oil refinery that is contracted to supply the UK for 25 years be accounted as a UK targeted cyber attack and this foreign-based asset should be accounted for as part of the UK critical infrastructures list ?
How an attack on Qatar’s Raslaffan industrial area will be considered “which if destroyed, disrupted or exploited might have an immediate and deleterious effect on the United States.” as per another cable “http://www.wikileaks.ch/cable/2009/03/09DOHA214.html”
Looking at those international interdependencies from the CIIP point of view is certainly very interesting,
Another Cable Quote ” In addition to a list of critical domestic CI/KR, the NIPP requires compilation and annual update of a comprehensive inventory of CI/KR that are located outside U.S. borders and whose loss could critically impact the public health, economic security, and/or national and homeland security of the United States. DHS in collaboration with State developed the Critical Foreign Dependencies Initiative (CFDI)to identify these critical U.S. foreign dependencies — foreign CI/KR that may affect systems within the U.S. directly or indirectly. State is coordinating with DHS to develop the 2009 inventory, and the action request in Para. 13 represents the initial step in this process. ”
The full list of international Critical infrastructures [Below] include : ( Oil refineries, sea ports , Internet landing points, gas pipelines…etc) , Original Cable (Here)
———————————————————————————————————————
AFRICA Congo (Kinshasa): Cobalt (Mine and Plant) Gabon: Manganese – Battery grade, natural; battery grade, synthetic; chemical grade; ferro; metallurgical grade Guinea: Bauxite (Mine) South Africa: BAE Land System OMC, Benoni, South Africa Brown David Gear Industries LTD, Benoni, South Africa Bushveld Complex (chromite mine) Ferrochromium Manganese – Battery grade, natural; battery grade, synthetic; chemical grade; ferro; metallurgical grade Palladium Mine and Plant Platinum Mines Rhodium EAST ASIA AND THE PACIFIC Australia: Southern Cross undersea cable landing, Brookvale, Australia Southern Cross undersea cable landing, Sydney, Australia Manganese – Battery grade, natural; battery grade, synthetic; chemical grade; ferro; metallurgical grade Nickel Mines Maybe Faulding Mulgrave Victoria, Australia: Manufacturing facility for Midazolam injection. Mayne Pharma (fill/finish), Melbourne, Australia: Sole suppliers of Crotalid Polyvalent Antivenin (CroFab). China: C2C Cable Network undersea cable landing, Chom Hom Kok, Hong Kong C2C Cable Network undersea cable landing Shanghai, China China-US undersea cable landing, Chongming, China China-US undersea cable landing Shantou, China EAC undersea cable landing Tseung Kwan O, Hong Kong FLAG/REACH North Asia Loop undersea cable landing Tong Fuk, Hong Kong Hydroelectric Dam Turbines and Generators Fluorspar (Mine) Germanium Mine Graphite Mine Rare Earth Minerals/Elements Tin Mine and Plant Tungsten – Mine and Plant Polypropylene Filter Material for N-95 Masks Shanghai Port Guangzhou Port Hong Kong Port Ningbo Port Tianjin Port Fiji: Southern Cross undersea cable landing, Suva, Fiji Indonesia: Tin Mine and Plant Straits of Malacca Japan: C2C Cable Network undersea cable landing, Chikura, Japan C2C Cable Network undersea cable landing, Shima, Japan China-US undersea cable, Okinawa, Japan EAC undersea cable landing Ajigaura, Japan EAC undersea cable landing Shima, Japan FLAG/REACH North Asia Loop undersea cable landing Wada, Japan FLAG/REACH North Asia Loop undersea cable landing Wada, Japan Japan-US undersea cable landing, Maruyama, Japan Japan-US undersea cable landing Kitaibaraki, Japan KJCN undersea cable landing Fukuoka, Japan KJCN undersea cable landing Kita-Kyushu, Japan Pacific Crossing-1 (PC-1) undersea cable landing Ajigaura, Japan Pacific Crossing-1 (PC-1) undersea cable landing Shima, Japan Tyco Transpacific undersea cable landing, Toyohashi, Japan Tyco Transpacific undersea cable landing Emi, Japan Hitachi, Hydroelectric Dam Turbines and Generators Port of Chiba Port of Kobe Port of Nagoya Port of Yokohama Iodine Mine Metal Fabrication Machines Titanium Metal (Processed) Biken, Kanonji City, Japan Hitachi Electrical Power Generators and Components Large AC Generators above 40 MVA Malaysia: Straits of Malacca New Zealand: Southern Cross undersea cable landing, Whenuapai, New Zealand Southern Cross undersea cable landing, Takapuna, New Zealand Philippines: C2C Cable Network undersea cable landing, Batangas, Philippines EAC undersea cable landing Cavite, Philippines Republic of Korea: C2C Cable Network undersea cable landing, Pusan, Republic of Korea. EAC undersea cable landing Shindu-Ri, Republic of Korea FLAG/REACH North Asia Loop undersea cable landing Pusan, Republic of Korea KJCN undersea cable landing Pusan, Republic of Korea Hitachi Large Electric Power Transformers 230 – 500 kV Busan Port Singapore: C2C Cable Network undersea cable landing, Changi, Singapore EAC undersea cable landing Changi North, Singapore Port of Singapore Straits of Malacca Taiwan: C2C Cable Network undersea cable landing, Fangshan, Taiwan C2C Cable Network undersea cable landing, Tanshui, Taiwan China-US undersea cable landing Fangshan, Taiwan EAC undersea cable landing Pa Li, Taiwan FLAG/REACH North Asia Loop undersea cable landing Toucheng, Taiwan Kaohsiung Port EUROPE AND EURASIA Europe (Unspecified): Metal Fabrication Machines: Small number of Turkish companies (Durma, Baykal, Ermaksan) Austria: Baxter AG, Vienna, Austria: Immune Globulin Intravenous (IGIV) Octapharma Pharmazeutika, Vienna, Austria: Immune Globulin Intravenous (IGIV) Azerbaijan: Sangachal Terminal Baku-Tbilisi-Ceyhan Pipeline Belarus: Druzhba Oil Pipeline Belgium: Germanium Mine Baxter SA, Lessines, Belgium: Immune Globulin Intravenous (IGIV) Glaxo Smith Kline, Rixensart, Belgium: Acellular Pertussis Vaccine Component GlaxoSmithKline Biologicals SA, Wavre, Belgium: Acellular Pertussis Vaccine Component Port of Antwerp Denmark: TAT-14 undersea cable landing, Blaabjerg, Denmark Bavarian Nordic (BN), Hejreskovvej, Kvistgard, Denmark: SMALLPOX Vaccine Novo Nordisk Pharmaceuticals, Inc. Bagsvaerd, Denmark: Numerous formulations of insulin Novo Nordisk Insulin Manufacturer: Global insulin supplies Statens Serum Institut, Copenhagen, Denmark: DTaP (including D and T components) pediatric version France: APOLLO undersea cable, Lannion, France FA-1 undersea cable, Plerin, France TAT-14 undersea cable landing St. Valery, France Sanofi-Aventis Insulin Manufacturer: Global insulin supplies Foot and Mouth Disease Vaccine finishing Alstrom, Hydroelectric Dam Turbines and Generators Alstrom Electrical Power Generators and Components EMD Pharms Semoy, France: Cyanokit Injection GlaxoSmithKline, Inc. Evreux, France: Influenza neurominidase inhibitor RELENZA (Zanamivir) Diagast, Cedex, France: Olympus (impacts blood typing ability) Genzyme Polyclonals SAS (bulk), Lyon, France: Thymoglobulin Sanofi Pasteur SA, Lyon, France: Rabies virus vaccine Georgia: Baku-Tbilisi-Ceyhan Pipeline Germany: TAT-14 undersea cable landing, Nodren, Germany. Atlantic Crossing-1 (AC-1) undersea cable landing Sylt, Germany BASF Ludwigshafen: World’s largest integrated chemical complex Siemens Erlangen: Essentially irreplaceable production of key chemicals Siemens, GE, Hydroelectric Dam Turbines and Generators Draeger Safety AG & Co., Luebeck, Germany: Critical to gas detection capability Junghans Fienwerktechnik Schramberg, Germany: Critical to the production of mortars TDW-Gasellschaft Wirksysteme, Schroebenhausen, Germany: Critical to the production of the Patriot Advanced Capability Lethality Enhancement Assembly Siemens, Large Electric Power Transformers 230 – 500 kV Siemens, GE Electrical Power Generators and Components Druzhba Oil Pipeline Sanofi Aventis Frankfurt am Main, Germany: Lantus Injection (insulin) Heyl Chemish-pharmazeutische Fabrik GmbH: Radiogardase (Prussian blue) Hameln Pharmaceuticals, Hameln, Germany: Pentetate Calcium Trisodium (Ca DTPA) and Pentetate Zinc Trisodium (Zn DTPA) for contamination with plutonium, americium, and curium IDT Biologika GmbH, Dessau Rossiau, Germany: BN Small Pox Vaccine. Biotest AG, Dreiech, Germany: Supplier for TANGO (impacts automated blood typing ability) CSL Behring GmbH, Marburg, Germany: Antihemophilic factor/von Willebrand factor Novartis Vaccines and Diagnostics GmbH, Marburg, Germany: Rabies virus vaccine Vetter Pharma Fertigung GmbH & Co KG, Ravensburg, Germany (filling): Rho(D) IGIV Port of Hamburg Ireland: Hibernia Atlantic undersea cable landing, Dublin Ireland Genzyme Ireland Ltd. (filling), Waterford, Ireland: Thymoglobulin Italy: Glaxo Smith Kline SpA (fill/finish), Parma, Italy: Digibind (used to treat snake bites) Trans-Med gas pipeline Netherlands: Atlantic Crossing-1 (AC-1) undersea cable landing Beverwijk, Netherlands TAT-14 undersea cable landing, Katwijk, Netherlands Rotterdam Port Norway: Cobalt Nickel Mine Poland: Druzhba Oil Pipeline Russia: Novorossiysk Export Terminal Primorsk Export Terminal. Nadym Gas Pipeline Junction: The most critical gas facility in the world Uranium Nickel Mine: Used in certain types of stainless steel and superalloys Palladium Mine and Plant Rhodium Spain: Strait of Gibraltar Instituto Grifols, SA, Barcelona, Spain: Immune Globulin Intravenous (IGIV) Maghreb-Europe (GME) gas pipeline, Algeria Sweden: Recip AB Sweden: Thyrosafe (potassium iodine) Switzerland: Hoffman-LaRoche, Inc. Basel, Switzerland: Tamiflu (oseltamivir) Berna Biotech, Berne, Switzerland: Typhoid vaccine CSL Behring AG, Berne, Switzerland: Immune Globulin Intravenous (IGIV) Turkey: Metal Fabrication Machines: Small number of Turkish companies (Durma, Baykal, Ermaksan) Bosporus Strait Baku-Tbilisi-Ceyhan Pipeline Ukraine: Manganese – Battery grade, natural; battery grade, synthetic; chemical grade; ferro; metallurgical grade United Kingdom: Goonhilly Teleport, Goonhilly Downs, United Kingdom Madley Teleport, Stone Street, Madley, United Kingdom Martelsham Teleport, Ipswich, United Kingdom APOLLO undersea cable landing Bude, Cornwall Station, United Kingdom Atlantic Crossing-1 (AC-1) undersea cable landing Whitesands Bay FA-1 undersea cable landing Skewjack, Cornwall Station Hibernia Atlantic undersea cable landing, Southport, United Kingdom TAT-14 undersea cable landing Bude, Cornwall Station, United Kingdom Tyco Transatlantic undersea cable landing, Highbridge, United Kingdom Tyco Transatlantic undersea cable landing, Pottington, United Kingdom. Yellow/Atlantic Crossing-2 (AC-2) undersea cable landing Bude, United Kingdom Foot and Mouth Disease Vaccine finishing BAE Systems (Operations) Ltd., Presont, Lancashire, United Kingdom: Critical to the F-35 Joint Strike Fighter BAE Systems Operations Ltd., Southway, Plymouth Devon, United Kingdom: Critical to extended range guided munitions BAE Systems RO Defense, Chorley, United Kingdom: Critical to the Joint Standoff Weapon (JSOW) AGM-154C (Unitary Variant) MacTaggart Scott, Loanhead, Edinburgh, Lothian, Scotland, United Kingdom: Critical to the Ship Submersible Nuclear (SSN) NEAR/MIDDLE EAST Djibouti: Bab al-Mendeb: Shipping lane is a critical supply chain node Egypt: ‘Ayn Sukhnah-SuMEd Receiving Import Terminal ‘Sidi Kurayr-SuMed Offloading Export Terminal Suez Canal Iran: Strait of Hormuz Khark (Kharg) Island Sea Island Export Terminal Khark Island T-Jetty Iraq: Al-Basrah Oil Terminal Israel: Rafael Ordnance Systems Division, Haifa, Israel: Critical to Sensor Fused Weapons (SFW), Wind Corrected Munitions Dispensers (WCMD), Tail Kits, and batteries Kuwait: Mina’ al Ahmadi Export Terminal Morocco: Strait of Gibraltar Maghreb-Europe (GME) gas pipeline, Morocco Oman: Strait of Hormuz Qatar: Ras Laffan Industrial Center: By 2012 Qatar will be the largest source of imported LNG to U.S. Saudi Arabia: Abqaiq Processing Center: Largest crude oil processing and stabilization plant in the world Al Ju’aymah Export Terminal: Part of the Ras Tanura complex As Saffaniyah Processing Center Qatif Pipeline Junction Ras at Tanaqib Processing Center Ras Tanura Export Terminal Shaybah Central Gas-oil Separation Plant Tunisia: Trans-Med Gas Pipeline United Arab Emirates (UAE): Das Island Export Terminal Jabal Zannah Export Terminal Strait of Hormuz Yemen: Bab al-Mendeb: Shipping lane is a critical supply chain node SOUTH AND CENTRAL ASIA Kazakhstan: Ferrochromium Khromtau Complex, Kempersai, (Chromite Mine) India: Orissa (chromite mines) and Karnataka (chromite mines) Generamedix Gujurat, India: Chemotherapy agents, including florouracil and methotrexate WESTERN HEMISPHERE Argentina: Foot and Mouth Disease Vaccine finishing Bermuda: GlobeNet (formerly Bermuda US-1 (BUS-1) undersea cable landing Devonshire, Bermuda Brazil: Americas-II undersea cable landing Fortaleza, Brazil GlobeNet undersea cable landing Fortaleza, Brazil GlobeNet undersea cable landing Rio de Janeiro, Brazil Iron Ore from Rio Tinto Mine Manganese – Battery grade, natural; battery grade, synthetic; chemical grade; ferro; metallurgical grade Niobium (Columbium), Araxa, Minas Gerais State (mine) Ouvidor and Catalao I, Goias State: Niobium Chile: Iodine Mine Canada: Hibernia Atlantic undersea cable landing Halifax , Nova Scotia, Canada James Bay Power Project, Quebec: monumental hydroelectric power development Mica Dam, British Columbia: Failure would impact the Columbia River Basin. Hydro Quebec, Quebec: Critical irreplaceable source of power to portions of Northeast U. S. Robert Moses/Robert H. Saunders Power, Ontario: Part of the St. Lawrence Power Project, between Barnhart Island, New York, and Cornwall, Ontario Seven Mile Dam, British Columbia: Concrete gravity dam between two other hydropower dams along the Pend d’Oreille River Pickering Nuclear Power Plant, Ontario, Canada Chalk River Nuclear Facility, Ontario: Largest supplier of medical radioisotopes in the world Hydrofluoric Acid Production Facility, Allied Signal, Amherstburg, Ontario Enbridge Pipeline Alliance Pipeline: Natural gas transmission from Canada Maritime and Northeast Pipeline: Natural gas transmission from Canada Transcanada Gas: Natural gas transmission from Canada Alexandria Bay POE, Ontario: Northern border crossing Ambassador Bridge POE, Ontario: Northern border crossing Blaine POE, British Columbia: Northern border crossing Blaine Washington Rail Crossing, British Columbia Blue Water Bridge POE, Ontario: Northern border crossing Champlain POE, Quebec: Northern border crossing CPR Tunnel Rail Crossing, Ontario (Michigan Central Rail Crossing) International Bridge Rail Crossing, Ontario International Railway Bridge Rail Crossing Lewiston-Queenstown POE, Ontario: Northern border crossing Peace Bridge POE, Ontario: Northern border crossing Pembina POE, Manitoba: Northern border crossing North Portal Rail Crossing, Saskatchewan St. Claire Tunnel Rail Crossing, Ontario Waneta Dam, British Columbia: Earthfill/concrete hydropower dam Darlington Nuclear Power Plant, Ontario, Canada. E-ONE Moli Energy, Maple Ridge, Canada: Critical to production of various military application electronics General Dynamics Land Systems – Canada, London Ontario, Canada: Critical to the production of the Stryker/USMC LAV Vehicle Integration Raytheon Systems Canada Ltd. ELCAN Optical Technologies Division, Midland, Ontario, Canada: Critical to the production of the AGM-130 Missile Thales Optronique Canada, Inc., Montreal, Quebec: Critical optical systems for ground combat vehicles Germanium Mine Graphite Mine Iron Ore Mine Nickel Mine Niobec Mine, Quebec, Canada: Niobium Cangene, Winnipeg, Manitoba: Plasma Sanofi Pasteur Ltd., Toronto, Canada: Polio virus vaccine GlaxoSmithKile Biologicals, North America, Quebec, Canada: Pre-pandemic influenza vaccines French Guiana: Americas-II undersea cable landing Cayenne, French Guiana Martinique: Americas-II undersea cable landing Le Lamentin, Martinique Mexico: FLAG/REACH North Asia Loop undersea cable landing Tijuana, Mexico Pan-American Crossing (PAC) undersea cable landing Mazatlan, Mexico Amistad International Dam: On the Rio Grande near Del Rio, Texas and Ciudad Acuna, Coahuila, Mexico Anzalduas Dam: Diversion dam south of Mission, Texas, operated jointly by the U.S. and Mexico for flood control Falcon International Dam: Upstream of Roma, Texas and Miguel Aleman, Tamaulipas, Mexico Retamal Dam: Diversion dam south of Weslaco, Texas, operated jointly by the U.S. and Mexico for flood control GE Hydroelectric Dam Turbines and Generators: Main source for a large portion of larger components Bridge of the Americas: Southern border crossing Brownsville POE: Southern border crossing Calexico East POE: Southern border crossing Columbia Solidarity Bridge: Southern border crossing Kansas City Southern de Mexico (KCSM) Rail Line, (Mexico) Nogales POE: Southern border crossing Laredo Rail Crossing Eagle Pass Rail Crossing Otay Mesa Crossing: Southern border crossing Pharr International Bridge: Southern border crossing World Trade Bridge: Southern border crossing Ysleta Zaragosa Bridge: Southern border crossing Hydrofluoric Acid Production Facility Graphite Mine GE Electrical Power Generators and Components General Electric, Large Electric Power Transformers 230 – 500 kV Netherlands Antilles: Americas-II undersea cable landing Willemstad, Netherlands Antilles. Panama: FLAG/REACH North Asia Loop undersea cable landing Fort Amador, Panama Panama Canal Peru: Tin Mine and Plant Trinidad and Tobago: Americas-II undersea cable landing Port of Spain Atlantic LNG: Provides 70% of U.S. natural gas import needs Venezuela: Americas-II undersea cable landing Camuri, Venezuela GlobeNet undersea cable landing, Punta Gorda, Venezuela GlobeNet undersea cable landing Catia La Mar, Venezuela GlobeNet undersea cable landing Manonga, Venezuela [END TEXT OF LIST]
Stuxnet: and The Truth Shall Set You Free
A recent post on Symantec’s security Blog revealed a very crucial piece of information about Stuxnet, The information should definitely stop who ever is denying the fact that Stuxnet is a state sponsored “sabotage-ware” targeting a very special someone.
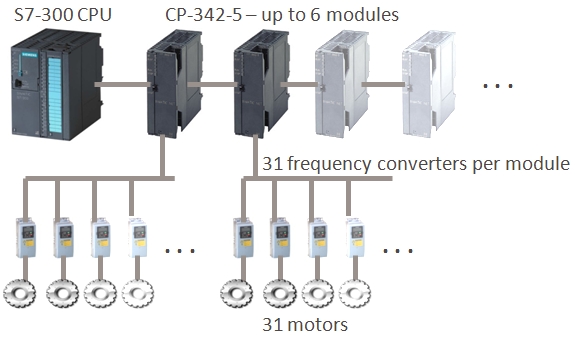
Symantec with the help of a Dutch Profibus expert can now prove that Stuxnet is looking for two specific Frequency converter drives one made by (Fararo Paya) of Iran and the other is (Vacon) of Finland.
Quote from Symantec’s blog: “Since our discovery that Stuxnet actually modifies code on PLCs in a potential act of sabotage, we have been unable to determine what the exact purpose of Stuxnet is and what its target was.”
“However, we can now confirm that Stuxnet requires the industrial control system to have frequency converter drives from at least one of two specific vendors, one headquartered in Finland and the other in Tehran, Iran. This is in addition to the previous requirements we discussed of a S7-300 CPU and a CP-342-5 Profibus communications module.”
and then they add: “Stuxnet monitors the current operating frequency of these motors, which must be between 807 Hz and 1210 Hz, before Stuxnet modifies their behavior. Relative to the typical uses of frequency converter drives, these frequencies are considered very high-speed and now limit the potential speculated targets of Stuxnet. We are not experts in industrial control systems and do not know all the possible applications at these speeds, but for example, a conveyor belt in a retail packaging facility is unlikely to be the target. Also, efficient low-harmonic frequency converter drives that output over 600Hz are regulated for export in the United States by the Nuclear Regulatory Commission as they can be used for uranium enrichment. We would be interested in hearing what other applications use frequency converter drives at these frequencies.”
So FACTs so far are the following:
– We are now able to describe the purpose of all of Stuxnet’s code.
– Stuxnet requires particular frequency converter drives from specific vendors, some of which may not be procurable in certain countries. ( In other words countries under international sanctions ).
– Stuxnet requires the frequency converter drives to be operating at very high speeds, between 807 Hz and 1210 Hz. (According to the US nuclear Commission – more than 600 Hz can be used in Uranium enrichment)
-While frequency converter drives are used in many industrial control applications, these speeds are used only in a limited number of applications. (Nuclear Applications is one of them).
-Stuxnet changes the output frequencies and thus the speed of the motors for short intervals over periods of months. Interfering with the speed of the motors sabotages the normal operation of the industrial control process. (Sabotage is the purpose)
– Stuxnet’s requirement for particular frequency converter drives and operating characteristics focuses the number of possible speculated targets to a limited set of possibilities. (The Special Someone Speaks Iranian)
The original Symantec Blog post HERE

Recent Comments